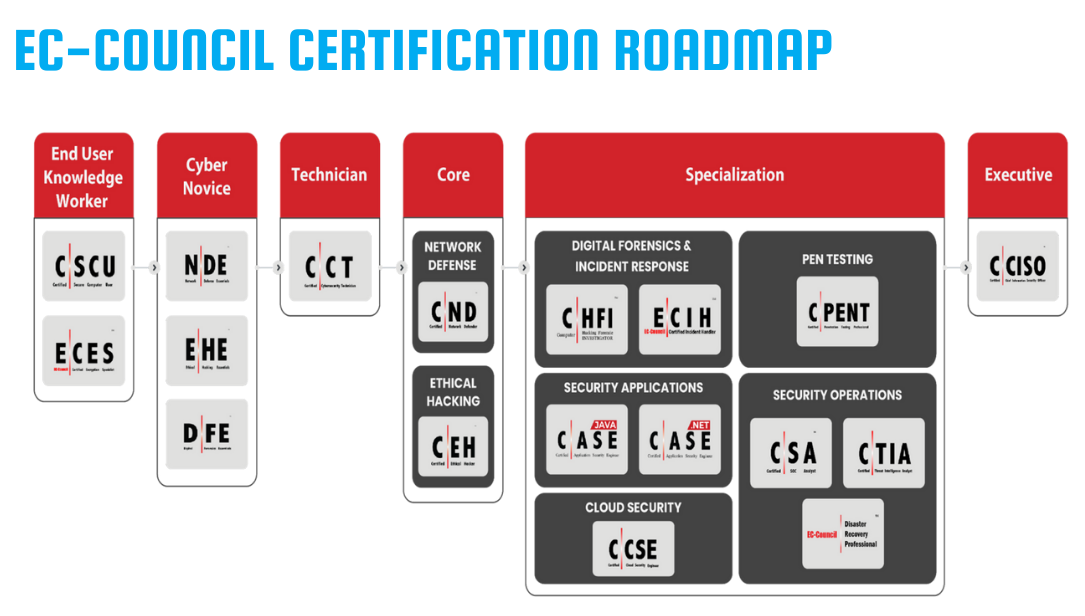
Who should join Certified Ethical Hacker (C|EH)?
The C|EH program gives you the knowledge and ability to protect databases, applications, networks, systems, and sensitive data from hostile hackers. The principles of scanning, enumeration, foot printing, reconnaissance, and ethical hacking will all be covered.
While CEH is a fantastic location to begin your cyber security career, admission to the
program requires some pre-requisite expertise. It is encouraged that you undertake the C|EH
after at least two years of experience in IT security. It is advised to join pre-requisite
courses such as C|CT. After finishing and becoming a certified ethical hacker, one can work in the fields described below:
- Mid-Level Information Security Auditor
- Cybersecurity Auditor
- Security Administrator
- IT Security Administrator
- Cyber Defense Analyst
- Vulnerability Assessment Analyst
- Warning Analyst
- Information Security Analyst 1
- Security Analyst L1
- Infosec Security Administrator
- Cybersecurity Analyst Level 1, Level 2, & Level 3
- Network Security Engineer
- SOC Security Analyst
- Security Analyst
- Network Engineer
- Senior Security Consultant
- Information Security Manager
- Senior SOC Analyst
- Solution Architect
- Cybersecurity Consultant

Course Lead Instructor
Enroll at Twinkle University!
Certified Ethical Hacker (C|EH) Instructor-led course will cost 500 USD. You will be provided with the items shown below for this course on enrollment:
- eBook - 24 months access
- iLab - 6 months access
- Exam Voucher - 12 months validity
- Face to face training - 40 hours
- 2 months installment option available

EC Council Certified Instructor will teach and train the course students on-campus. Twinkle University is not only the Academia partner of EC Council but also the approved Test Center for EC Council courses and therefore, exams for all the courses provided above can be scheduled and taken at anytime within office hours of the university.
Course Outline
| Module 01: Introduction to Ethical Hacking |
| Module 02: Foot printing and Reconnaissance |
| Module 03: Scanning Networks |
| Module 04: Enumeration |
| Module 05: Vulnerability Analysis |
| Module 06: System Hacking |
| Module 07: Malware Threats |
| Module 08: Sniffing |
| Module 09: Social Engineering |
| Module 10: Denial-of-Service |
| Module 11: Session Hijacking |
| Module 12: Evading IDS, Firewalls, and Honeypots |
| Module 13: Hacking Web Servers |
| Module 14: Hacking Web Applications |
| Module 15: SQL Injection |
| Module 16: Hacking Wireless Networks |
| Module 17: Hacking Mobile Platforms |
| Module 18: IoT and OT Hacking |
| Module 19: Cloud Computing |
| Module 20: Cryptography |
| Module 21: Business Continuity and Disaster Recoverys |
| Module 22: Risk Management |
Technologies covered in this course








Tutors
Meet our Tutors

Tr. Hein Nay Zaw
EC-Council-Certified Instructor
Knowledgeable and skilled instructor who is dedicated to cybersecurity education. Experienced in
both offensive and defensive security
QUALIFICATIONS
B.Sc.(Hons), Greenwich University
NCC L5DC
NCC L4DC
C|EHv12 (EC Council)
C|NDv2 (EC Council)
C|CTv1 (EC Council)
C|SCUv2 (EC Council)
PCNSE
CC (ISC)²
NSE 1,2,3 (Fortinet)
CCNP (ENARSI)
JNCIA (Juniper Networks)
